Intelligent Cybersecurity for Your Business Growth
Cybersecurity is the body of technologies, processes, and practices designed to protect networks, computers, and data from attack, damage, and unauthorized access. Cyber-attacks are one of the defining security threats of our age and cyber security a growing priority for business and governments alike. The internet’s transformation of both our personal lives and the world of commerce has created boundless opportunities for hackers with a wide range of motives and an even broader array of tools. From phishing and clickjacking to ransomware, direct-access attacks and denial of service attacks (DoS) the threats keep on evolving and emerging.
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users; or interrupting normal business processes.Implementing effective cybersecurity measures is particularly challenging today because there are more devices than people, and attackers are becoming more innovative.
A successful cybersecurity approach has multiple layers of protection spread across the computers, networks, programs, or data that one intends to keep safe. In an organization, the people, processes, and technology must all complement one another to create an effective defense from cyber attacks. A unified threat management system can automate integrations across select Cyber Security products and accelerate key security operations functions: detection, investigation, and remediation. Technology is essential to giving organizations and individuals the computer security tools needed to protect themselves from cyber attacks. Three main entities must be protected: endpoint devices like computers, smart devices, and routers; networks; and the cloud. Common technology used to protect these entities include next-generation firewalls, DNS filtering, malware protection, antivirus software, and email security solutions.
Delivering Intelligence Cybersecurity
Network Security
Wireless Network Security
Wireless Network Security

Network Security protects network traffic by controlling incoming and outgoing connections to prevent threats from entering or spreading on the network.
Wireless Network Security
Wireless Network Security
Wireless Network Security

AI-powered Wi-Fi for today’s experience edge with Sixth generation Wi-Fi and smart innovations simplify IT and enhance user experiences.
SD-WAN
Wireless Network Security
Application Security

Enterprise SD-WAN meets the No.1 most secure NextGen Firewall. New business models drive the need for a new network model.
Application Security
Data Loss Prevention (DLP)
Application Security

Application security is the process of developing, adding, and testing security features within applications to prevent security vulnerabilities against threats such as unauthorized access and modification.
Information Security
Data Loss Prevention (DLP)
Data Loss Prevention (DLP)

Information Security refers to the processes and methodologies which are designed and implemented to protect print, electronic, or any other form of confidential, private and sensitive information or data from unauthorized access, use, misuse, disclosure, destruction, modification, or disruption.
Data Loss Prevention (DLP)
Data Loss Prevention (DLP)
Data Loss Prevention (DLP)

Data Loss Prevention (DLP) protects data by focusing on the location, classification and monitoring of information at rest, in use and in motion.
Cloud Security
Cloud Security provides protection for data used in cloud-based services and applications.
IDS/IPS

Intrusion Detection Systems (IDS) or Intrusion Prevention Systems (IPS) work to identify potentially hostile cyber activity.
Identity and Access Management (IAM)
Virtual Private Network (VPN) and Encryption

Identity and Access Management (IAM) use authentication services to limit and track employee access to protect internal systems from malicious entities.
Virtual Private Network (VPN) and Encryption
Virtual Private Network (VPN) and Encryption
Virtual Private Network (VPN) and Encryption

Virtual Private Network (VPN) and Encryption is the process of encoding data to render it unintelligible, and is often used during data transfer to prevent theft in transit.
Antivirus/anti-malware
Virtual Private Network (VPN) and Encryption
Antivirus/anti-malware

Antivirus/anti-malware solutions scan computer systems for known threats. Modern solutions are even able to detect previously unknown threats based on their behavior.
Protect Against Threats: Even Before They Reach You

Phishing
Phishing is the practice of sending fraudulent emails that resemble emails from reputable sources. The aim is to steal sensitive data like credit card numbers and login information. It’s the most common type of cyber attack. You can help protect yourself through education or a technology solution that filters malicious emails.
Ransomware
Ransomware is a type of malicious software. It is designed to extort money by blocking access to files or the computer system until the ransom is paid. Paying the ransom does not guarantee that the files will be recovered or the system restored.

Malware
Malware is a type of software designed to gain unauthorized access or to cause damage to a computer.

Social Engineering
Social engineering is a tactic that adversaries use to trick you into revealing sensitive information. They can solicit a monetary payment or gain access to your confidential data. Social engineering can be combined with any of the threats listed above to make you more likely to click on links, download malware, or trust a malicious source.

Man-in-the-middle attack
Man-in-the-middle (MitM) attacks, also known as eavesdropping attacks, occur when attackers insert themselves into a two-party transaction. Once the attackers interrupt the traffic, they can filter and steal data. Two common points of entry for MitM attacks:
- On unsecure public Wi-Fi, attackers can insert themselves between a visitor’s device and the network. Without knowing, the visitor passes all information through the attacker.
- Once malware has breached a device, an attacker can install software to process all of the victim’s information.

Denial-of-service (DoS) attack
A denial-of-service attack floods systems, servers, or networks with traffic to exhaust resources and bandwidth. As a result, the system is unable to fulfill legitimate requests. Attackers can also use multiple compromised devices to launch this attack. This is known as a distributed-denial-of-service (DDoS) attack.
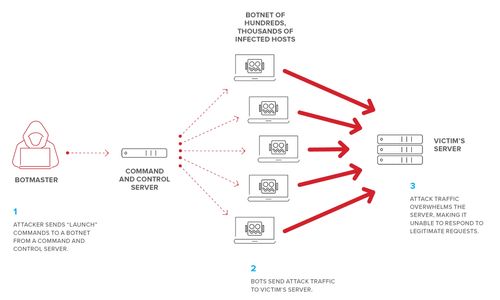
Distributed Denial-of-Service (DDoS) attack
Denial-of-service (DDoS) aims at shutting down a network or service, causing it to be inaccessible to its intended users. The attacks accomplish this mission by overwhelming the target with traffic or flooding it with information that triggers a crash. In both situations, the DoS onslaught denies legitimate users such as employees, account holders, and members of the resource or service they expected.
DDoS attacks are often targeted at web servers of high-profile organizations such as trade organizations and government, media companies, commerce, and banking. Although these attacks don’t result in the loss or theft of vital information or other assets, they can cost a victim lots of money and time to mitigate. DDoS is often used in combination to distract from other network attacks.

SQL injection
A Structured Query Language (SQL) injection occurs when an attacker inserts malicious code into a server that uses SQL and forces the server to reveal information it normally would not. An attacker could carry out a SQL injection simply by submitting malicious code into a vulnerable website search box.

Zero-day exploit
A zero-day exploit hits after a network vulnerability is announced but before a patch or solution is implemented. Attackers target the disclosed vulnerability during this window of time. Zero-day vulnerability threat detection requires constant awareness.

DNS Tunneling
DNS tunneling utilizes the DNS protocol to communicate non-DNS traffic over port 53. It sends HTTP and other protocol traffic over DNS. There are various, legitimate reasons to utilize DNS tunneling. However, there are also malicious reasons to use DNS Tunneling VPN services. They can be used to disguise outbound traffic as DNS, concealing data that is typically shared through an internet connection. For malicious use, DNS requests are manipulated to exfiltrate data from a compromised system to the attacker’s infrastructure. It can also be used for command and control callbacks from the attacker’s infrastructure to a compromised system.

Drive-by Attack
A drive-by attack is a common method of distributing malware.
A cyber attacker looks for an insecure website and plants a malicious script into PHP or HTTP in one of the pages. This script can install malware into the computer that visits this website or become an IFRAME that redirects the victim’s browser into a site controlled by the attacker. In most cases, these scripts are obfuscated, and this makes the code to be complicated to analyze by security researchers. These attacks are known as drive-by because they don’t require any action on the victim’s part except visiting the compromised website. When they visit the compromised site, they automatically and silently become infected if their computer is vulnerable to the malware, especially if they have not applied security updates to their applications.

Trojan Horses
A Trojan is a malicious software program that misrepresents itself to appear useful. They spread by looking like routine software and persuading a victim to install. Trojans are considered among the most dangerous type of all malware, as they are often designed to steal financial information.

Cross Site Scripting
Cross-site scripting (XSS) is a kind of injection breach where the attacker sends malicious scripts into content from otherwise reputable websites. It happens when a dubious source is allowed to attach its own code into web applications, and the malicious code is bundled together with dynamic content that is then sent to the victim’s browser.
Malicious code is usually sent in the form of pieces of Javascript code executed by the target’s browser. The exploits can include malicious executable scripts in many languages including Flash, HTML, Java, and Ajax. XSS attacks can be very devastating, however, alleviating the vulnerabilities that enable these attacks is relatively simple.

Password Attack
A password attack simply means an attempt to decrypt or obtain a user’s password with illegal intentions. Crackers can use password sniffers, dictionary attacks, and cracking programs in password attacks. There are few defense mechanisms against password attacks, but usually, the remedy is inculcating a password policy that includes a minimum length, frequent changes, and unrecognizable words.
Password attacks are often carried out by recovering passwords stored or exported through a computer system. The password recovery is usually done by continuously guessing the password through a computer algorithm. The computer tries several combinations until it successfully discovers the password.

Eavesdropping Attack
Eavesdropping attacks start with the interception of network traffic.
An Eavesdropping breach, also known as snooping or sniffing, is a network security attack where an individual tries to steal the information that smartphones, computers and other digital devices send or receive This hack capitalizes on unsecured network transmissions to access the data being transmitted. Eavesdropping is difficult to detect since it doesn’t cause abnormal data transmissions.
These attacks target weakened transmissions between the client and server that enables the attacker to receive network transmissions. An attacker can install network monitors such as sniffers on a server or computer to perform an eavesdropping attack and intercept data as it is being transmitted. Any device within the transmitting and receiving network is a vulnerability point, including the terminal and initial devices themselves. One way to protect against these attacks is knowing what devices are connected to a particular network and what software is run on these devices.

Birthday attack
A birthday attack is a type of cryptographic attack that exploits the mathematics behind the birthday problem in probability theory. This attack can be used to abuse communication between two or more parties. The attack depends on the higher likelihood of collisions found between random attack attempts and a fixed degree of permutations.

Insider Threats
Not every network attack is performed by someone outside an organization. Inside attacks are malicious attacks performed on a computer system or network by an individual authorized to access the system. Insiders that carry out these attacks have the edge over external attackers since they have authorized system access. They may also understand the system policies and network architecture. Furthermore, there is less security against insider attacks since most organizations focus on defending against external attacks. Insider threats can affect all elements of computer security and range from injecting Trojan viruses to stealing sensitive data from a network or system. The attackers may also affect the system availability by overloading the network or computer processing capacity or computer storage, resulting in system crashes.

Brute-Force and Dictionary Network Attacks
Dictionary and brute-force attacks are networking attacks whereby the attacker attempts to log into a user’s account by systematically checking and trying all possible passwords until finding the correct one.
The simplest method to attack is through the front door since you must have a way of logging in. If you have the required credentials, you can gain entry as a regular user without creating suspicious logs, needing an unpatched entry, or tripping IDS signatures. If you have a system’s credentials, your life is even simplified since attackers don’t have these luxuries.
Copyright © 2025 IQSOFT.ai - All Rights Reserved.
